Information Flow for Trusted Execution
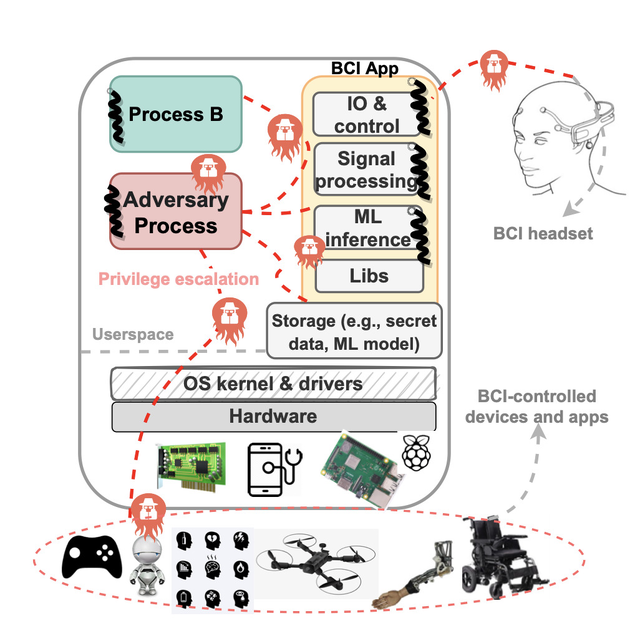
There is now increased hardware support for improving the security and performance of privilege separation and compartmentalization techniques such as process-based sandboxes, trusted execution environments, and intra-address space compartments. We dub these "hetero-compartment environments" and observe that existing system stacks still assume single-compartment models (i.e. user space processes), leading to limitations in using, integrating, and monitoring heterogeneous compartments from a security and performance perspective. This project explores how we might deploy techniques such as fine-grained information flow control (DIFC) to allow developers to securely use and combine compartments, define security policies over shared system resources, and audit policy violations and perform digital forensics across hetero-compartments.
The primary focus of this work was conducting by Zahra Tarkhani in her PhD work on new hypervisor/OS/userspace interfaces for compartmentalization that could take advantage of TEE hardware (see Secure Programming with Dispersed Compartments).
Since that work has been completed, I've also been exploring the use of DIFC labels as part of Planetary Computing, in order to encrypt and control access to datasets across organisation boundaries. This work is still in the exploratory stages with Patrick Ferris and Michael Dales.